
Dell KACE Desktop Authority Management Suite
Centralized, secure and consistent management of the Windows user environment

Sorry, this product is no longer available, Please contact us for a replacement solution.
Overview:
Today’s sophisticated users are demanding more flexibility in IT operations, but administrators must still maintain a secure and consistent user environment. They can no longer rely on the traditional model of managing only the machine; each user needs to be granted the right access to the right resources regardless of the device used. This means that even small businesses are dealing with hundreds of user environments. In addition, administrators must control application privileges appropriately, ensuring that they can run without full local administrator access.
Desktop Authority Management Suite is comprised of two solutions: Desktop Authority Standard and Privilege Manager. Together, these desktop management software solutions enable admins to proactively provision and manage the Windows user environment. With this suite, you can easily create a secure, consistent environment for each user, and ensure that applications run with only the privileges and access needed.
Easily target user configurations
Easily establish who among the tens, hundreds or thousands of users within an organization should get a particular configuration setting. Let Desktop Authority and Privilege Manager ensure that the right configurations and administrative privileges are always presented to the right users, no matter where they are or how they log in.
Customize user-based configurations without logon scripts
Combine traditional desktop management software with user environment management for a simple yet robust way to automate user configurations. Easily configure each user environment as a unique mix of OS, applications, printers and more, as well as corresponding drivers, Registry edits, proxy settings or other configuration changes.
Balance security with user productivity
Selectively target configurations and privileges to ensure security is balanced with productivity. You can keep sensitive data from exiting your organization and vulnerabilities from being introduced by end users, without limiting capabilities or causing productivity issues for users on daily tasks.
Keep mobile users working while also maintaining a secure network
Support users anywhere. Remotely manage issues “behind the screen” using more than 30 different management tasks without disturbing users or remote control the desktop to resolve a problem.
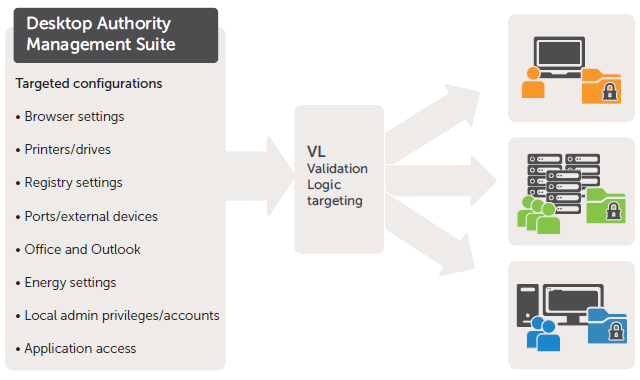
Patented Validation Logic technology targets and enforces configurations and settings for user environment management.
Features:
Targeted criteria-based configuration settings
Easily define configurations based on user or organizational identity, type of machine and operating system, virtual or physical environment, connection type and more. Desktop Authority presents more than 40 predefined criteria to automatically deploy unique desktop configurations. Those criteria encompass the user, the computer, type of desktop (physical, terminal or virtual) and deployment timing.
Easy user management
Automate updates of targeting criteria. Desktop Authority evaluates the targeting criteria at the time the profile is applied, and changes targeting automatically when users move to different locations, log in to different machines or access Terminal Servers. If a user changes something, Desktop Authority will re-apply the desired setting the next time the profile refreshes.
Configuration of groups and elements
Configure and deploy more than 30 unique elements quickly and easily, and to the appropriate subset of the organization. Combine configuration elements into profiles to represent locations and groups of users—even a disaster recovery configuration—to make it even easier to meet the current business needs of your users.
Targeted administrative privileges
Avoid the need to create and maintain many overlapping security groups to try and target rules at the desired targets. Privilege Manager uses a subset of Validation Logic criteria to target elevated administrative privileges for users and applications that need this access to be productive.
Maintained privileges regardless of location
Keep your mobile users working, and your network secure. Validation Logic's advanced targeting features ensure the correct elevation settings always apply when a user travels between offices.
Elimination of logon scripts
Select (instead of code) desktop configurations through a simple web interface, and avoid taking the time to write and test—as well as execute—custom logon scripts at each login. Selections include drive mappings, Registry settings, Office and Outlook settings, printers, message boxes, PC power management and more.
Reduced, simplified Group Policy management
Precisely target the deployment of 2,400-plus available Group Policies. Desktop Authority parses ADM/ADMX templates and allows deployment of Windows configuration settings using more than 40 criteria of Validation Logic.
Controlled Internet browser behaviors
Bring virtually every aspect of Internet Explorer and Mozilla Firefox under your direct control with Desktop Authority's Internet Browser management object. With more and more applications delivered via an Internet browser, cohesively managing browser configurations is a mission-critical task.
Configuration across various environments
Gain precise configuration control across every delivery infrastructure – physical, virtual, or published – all from a single solution. Physical desktops are no longer the only devices users work with. Today's business computing optimizes user interactions across virtual desktops and published environments.
Secure installation of trusted apps
Allow users to simultaneously install the latest version of Adobe Reader or apply the latest Java update themselves with Privilege Manager. Simultaneously maintain endpoint security by preventing installation of viruses and unwanted apps. Users are also able to request elevated privileges by sending a request to the administrator who can deny or approve and notify the user on request status.
Endpoint lock down
Control both device usage (like flash drives, printers, cameras and mobile devices) as well as port access (such as serial, infrared, USB and more)—all according to each user's unique levels of authentication and access—with the Desktop Authority USB and Port Security component. Choose which level of access you provide by targeting Read, Write, Full Access or Full Deny. Secure user environments aren't only about the software and permissions configured for a user. They're also about the devices each user can introduce into that configuration.
Quick admin-privilege applications discovery
Discover which applications being used require administrative privileges with Privilege Manager. Once discovered, you can easily create privilege elevation rules so users can use applications without disruption.
Centralized deployment of remote management
Ensure security, privacy and productivity. All remote desktop management functionality is deployed as part of the desktop configuration, complete with multiple security and user experience settings.
Management of remote user desktops
Enable remote Windows support professionals using any standard Java-enabled browser over a 128-bit SSL session to work "behind the screen" to resolve issues without needing to interact with the user. Save time and prevent frustration, while allowing user productivity to remain high.
Remote control of user desktops
Enable the same browser-based support session to be used to establish IT remote control or remote viewing of the desktop that needs attention when issues require the support professional to interact with the user. IM with users during the session and, if needed, blank the screen when entering credentials.
User, device, and admin control
Easily determine whether privilege policies need modification to meet compliance requirements by gathering all privilege usage information into a central database and run domain-level analysis. Desktop Authority provides turnkey and custom reports on user activity by collecting information about each user and computer under management. The USB and Port Security component provides reporting on access and details on transferred data.
Specifications:
| Desktop Authority Standard | |
|---|---|
| Server Requirements | |
| Operating systems |
|
| Domain controllers |
|
| Database server | Microsoft SQL Server version 2005 or higher |
| Installed if necessary |
|
| Client Requirements | |
| Browser supported |
|
| Screen resolution | 1024x768 |
| Software application |
|
| User Permissions | |
| User permission |
|
| Privilege Manager | |
|---|---|
| Console Requirements | |
| System requirements |
|
| Operating systems |
|
| Reporting |
|
| Network | Privilege Manager should be deployed as a part of the Active Directory infrastructure. |
| User permissions |
|
| Client Requirements | |
| Operating systems |
|
Documentation:
Dell KACE Desktop Authority Management Suite Data Sheet (.PDF)

